Publish Date - October 7th, 2023
|Last Modified - October 7th, 2023
The Internet has brought us many advantages, from making information easily accessible to connecting us with people worldwide.
However, with these conveniences come risks. Malware, phishing attacks, credit card scams, identity theft are all regularly occurrences for people that are unaware. Cyber criminals will try all sorts of strategies to access your sensitive information.
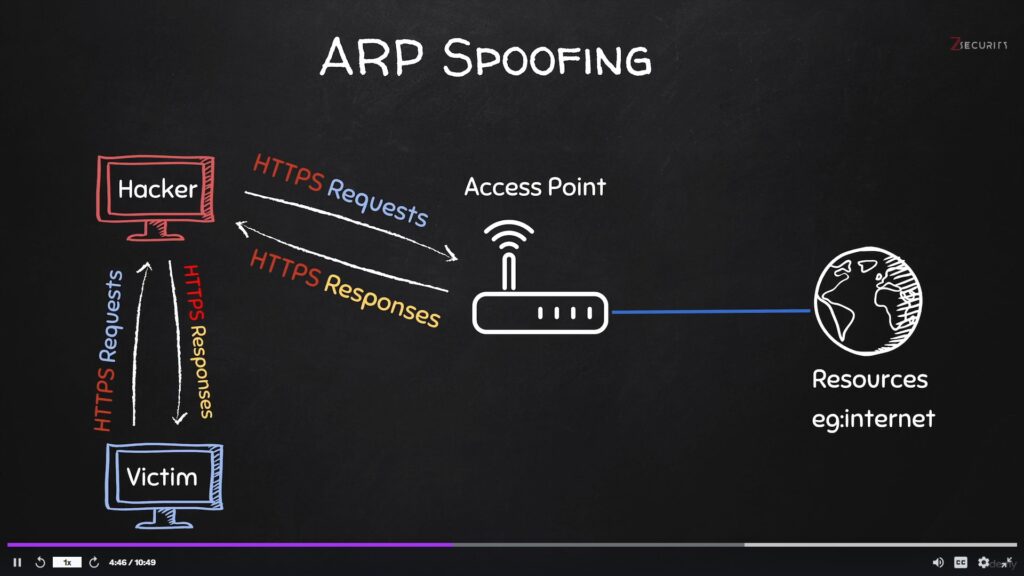
While phishing usually involves deceiving individuals into revealing their personal information through fraudulent emails, pharming redirects users either with a DNS change or some sort of spoofing strategy to fake websites without their knowledge to steal data.
Protecting yourself from these threats requires proactive measures, which we will delve into below.
1. Find Relevant Cybersecurity Help

Navigating the digital world’s safety pitfalls is not something you have to do alone. You can, and should, seek professional guidance.
Acquiring the services of professionals who specialize in online security can save you from potential risks.
How to find a reputable protection company
When looking for experts to help secure your online activities, it’s vital to seek out reputable companies.
A credible firm will offer comprehensive solutions that are tailored to your specific needs. They will perform a security audit, recommend appropriate measures, and often provide monitoring services to detect any unusual activities.
Look for reviews and testimonials as well as any industry awards or recognitions the company may have.
While it’s tempting to go for the least expensive option, remember that you get what you pay for. Opt for a balance between cost and quality services.
What types of support should you look for?
A good company will have the following types of security measures:
- Anti-phishing technologies and strategies
- Security awareness training
- Multiple firewalls and antivirus software (if providing actual security)
- Appropriate data sanitation of personal identifiable information like account numbers, social security numbers and general personal data.
You also want continuous support is equally crucial as even the best security systems can sometimes fall short.
A reputable company will offer ongoing support, frequently updating your security measures to counter new threats.
Make sure to ask whether they provide 24/7 customer support and how they handle emergency situations.
2. Keep Your Software Updated
If you’re in web development or even in marketing in-general, you know the importance of keeping your tools up-to-date. Keeping your operating system and software updated is one of the easiest yet most effective ways to protect yourself against phishing and pharming.
Importance Of Regular Updates
Software updates often come with patches that fix security vulnerabilities. Hackers are always on the lookout for outdated systems which are easier to breach.
Updating your software closes these loopholes, making it difficult for unauthorized users to gain access to your system. Ransomware and spyware (like Trojan horses) are regularly caused by out of date software that is vulnerable. The hacker can upload or inject a payload into your computer and network, or you just visit a malicious website.
Make it a habit to update your software whenever new versions are released.
Automatic Updates And Patches
Some people find the process of updating software tedious and time-consuming. However, most modern systems offer automatic updates, requiring little to no effort from the user. Take advantage of this feature by enabling automatic updates. This ensures that your system is always up-to-date without needing your constant intervention.
3. Be Skeptical Of Unsolicited Communications
If you receive an email, text, or any form of unsolicited communication asking for personal information, be extremely cautious. Due to social media, social engineering has become even easier. Scammers, once they get your phone number are able to impersonate bank personnel, business employees (like Amazon) and even the government officials.
From there, they will probe anything online that they can find trying to use your ip address and social media to catch you off-guard.
Verify Before You Trust
Always verify the source before divulging any information. Double-check the sender’s email address, look for any spelling mistakes, and be wary of links or attachments in the message. You can also do a quick search on the person who’s talking. Ask them where they’re from and to send you credentials. Most financial institutions will never ask for financial information upfront or even in email.
It’s always better to be skeptical and take the time to verify rather than falling victim to a scam.
Use Multi-Factor Authentication
Multi-factor authentication (MFA) adds an additional layer of security. Even if someone gains access to your password, they would still need a second form of identification to get into your account.
This could be a text message sent to your phone or a biometric identification like a fingerprint. Always enable MFA wherever possible. Most bank accounts and login credentials have this implemented to stop users
4. Secure Your Network

Your network is the gateway to your online activities. Ensuring that it is secure minimizes the risks associated with phishing and pharming. Data breaches are regular occurence in today’s age with hackers using pop-ups on fake sites, SMS scams and even Vishing (voice hacking) to try to get access to your sensitive data.
Use Strong Passwords And Change Them Regularly
A strong password is your first line of defense. It should be a mix of alphabets, numbers, and special characters. Change your passwords regularly and do not reuse old ones. Also, if you use multiple apps, try not to use the same password or even variations of the same password. This will limit the effectiveness of the phishing scams if there is a data breach.
Use A Virtual Private Network (VPN)
A VPN encrypts your internet connection, making it difficult for hackers to intercept your data.
It’s particularly useful when using public Wi-Fi, which is often less secure and more prone to attacks.
5. Educate And Train Those Around You
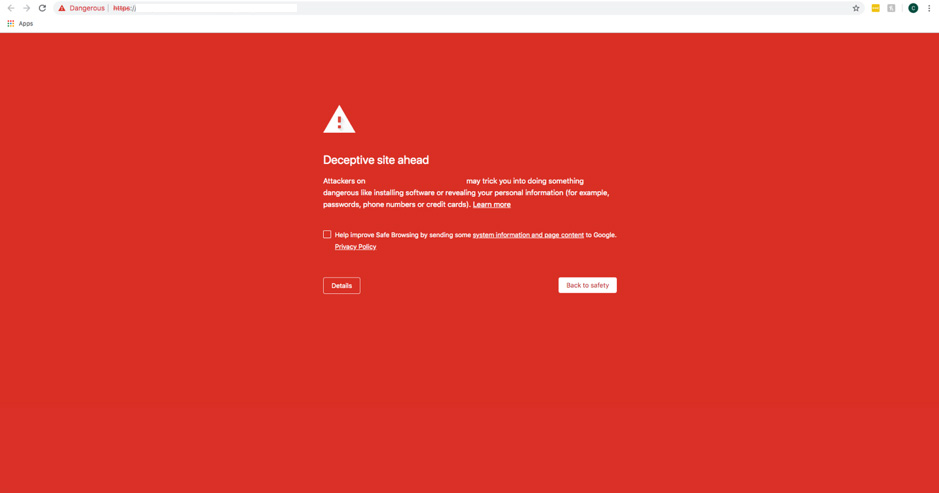
Ignorance is often the biggest enabler of cybercrime. By educating and training the people around you, you can create a more secure environment for everyone involved. If a login page looks funny or the functionality of a website you visit seems strange, make sure to check the domain name o the website before you put your credentials in. Also, check your address bar to ensure that there aren’t any DNS cache parameters that may surface data to a website that is hacked.
Create Awareness
Talk to your family, friends, and colleagues about the importance of online security. Share articles, videos, and other educational resources. Knowledge is power; the more people are aware of the risks, the less likely they are to fall victim to scams.
Regular Training Sessions
If you’re running a business, regular training sessions for your employees can make a huge difference. Make sure they know how to spot phishing emails and what steps to take if they suspect a cyberattack.
Take the plunge – become an ethical hacker
You can also take an even more aggressive stance and become an ethical hacker. Learn to code in Python, Java, C++ and then learn how to do penetration testing and other unique skills, so you can be better prepared if you’re pharmed or phished.
Final Remarks
Navigating the complexities of online security in today’s digital age is a critical task that should never be overlooked or underestimated. The threats posed by phishing and pharming are not merely theoretical but have real-world consequences that could affect your financial stability, personal privacy, and overall peace of mind.
While the landscape of cyber threats continues to evolve, the principles for maintaining a secure digital life remain constant: vigilance, education, and proactive action.
Taking steps to find a reputable protection company for personalized guidance isn’t just a recommendation but a necessity for complete online security.
The role of continuous support and up-to-date security measures cannot be overstated, given the evolving nature of cyber threats.
Furthermore, the need for keeping your software updated is an essential habit that serves as an additional buffer against external threats. It may seem trivial, but staying current can mean the difference between vulnerability and security.
FAQs
How do we avoid phishing and pharming attacks give examples?
You can avoid phishing and pharming attacks like someone saying you won a free Yeti cooler, by ensuring that you’re only opening links from reputable emails. Always, look at the domain name that’s sending you the email.
What is the best prevention from phishing and pharming?
While there are a number of AI tools coming out combat phishing and pharming, the best way to combat this attack is knowledge and situational awareness when dealing with these issues. If you’re unaware whether an email is a malicious email, this is already a cause for concern.
